Our recommendations are: Choose a strong password with a password generator, use a password manager, never re-use a password, ensure you have backups, enable full disk encryption (and for Windows enable EFS encryption for the Xecrets Ez [Beta] application directory).
Read on for detailed information, and some other options.
File encryption with Xecrets Ez [Beta] or Xecrets Command Line [Beta] will make the information contained in the encrypted files unavailable to anyone who does not know the password used to encrypt them. While absolute security is impossible to achieve, it can still be further improved by adding additional layers and understand where points of attack still exist.
Here you'll find some tips about how to add additional layers of security, such as full hard drive encryption, RAM disk drives for temporary files and perhaps most importantly: the often misunderstood importance of backups to achieve not only protection against unauthorized disclosure of your information, but also to protect it against loss or destruction.
In the end, essentially all encryption falls back to a password or a passphrase. Even when there's a hardware stored key involved, it's typically protected by... a password. This is especially true for all mainstream file, volume and disk encryption tools, Xecrets Ez [Beta] etc included.
When you read that someone's social media account has been hacked, what has actually happened almost every time is not that it's a 'hack' in the sense that some whiz-kid has exploited a vulnerability. What most likely did happen is that someone guessed the password, or got the users password from some other service, and the user re-used the same password for the account that was 'hacked'.
For example, when the Twitter (now X) account of a not-to-be-mentioned-by-name former president of the United States was 'hacked', someone simply guessed that the password was 'maga2020!' - and it was.
The moral of the story is that when you use a password to protect anything you care about, and if you're using encryption it's a fair guess that you do, it must be hard to guess! There are many strategies on how to choose a strong password, but the best one is to use a password generator, a password manager, and never use the same password twice.
Important: Encryption only protects information from being disclosed to unauthorized parties. It does not protect from deletion or other forms of loss or destruction, including being held hostage by ransomware.
Your only protection against data loss are backups. You should have a backup system that ensures you perform periodic backups, and that you store them in a different location than the original. If the primary location is a device, such as a desktop computer, the cloud is a good location or a removable drive that is stored in a different physical location. If the primary location instead is already the cloud, store the backup in another cloud, or on a local device.
Of course, you should protect the backup from unauthorized disclosure by encrypting it with for example Xecrets Command Line [Beta], it's a perfect application for scripted or programmatic file encryption. Files that are already encrypted with Xecrets Ez [Beta] does not have this problem, they can be backed up as-is without further protection.
Full disk encryption is the perfect complement to file encryption. While full disk encryption will keep your information safe on your own device, that's also the limit of the protection offered. As soon as your file leaves your device, perhaps in an email, or being uploaded or synchronized to the cloud, or copied to a different drive or device as a backup there is no longer any protection at all for the file.
In contrast, file encryption such as ours, the protection always follows the file. Regardless of how it's moved, copied, synchronized it stays encrypted and it stays protected.
Full disk encryption is typically completely transparent and thus a no-brainer to use. You won't even notice it's there, so there's really no reason not to use it. It'll protect your data in the case your device is lost or stolen.
There are many limits to full disk encryption in addition to it only being relevant for data as long as it stays on the disk. The most important one being that since access is tied to the computer, any software operating on it once it's started will also have access, this includes information stealing malware. The exposure with file encryption is much smaller, typically limited to files that are temporarily decrypted for use in the moment.
In relation to file encryption, the most important benefit of full disk encryption is that data that is temporarily decrypted will remain protected even if you do lose your device.
To summarize - enable full hard drive encryption on your drive.
For Windows, there is both device encryption, and standard BitLocker encryption. They are very similar, so use the version that is supported on your device, and follow the instructions.
Apple macOS has built in support in several layers, but it's always recommended to turn on FileVault disk encryption.
As always, since Linux is such a fragmented space, there are dozens if not hundreds of different solutions depending on your requirements and distribution used. Some distributions support it out of the box, others require you to choose and install it. Do a search for linux solutions in general, or for LUKS encryption as it appears to be a common choice and make your decision accordingly.
Another option, which has the advantage of being more selective, is to enable the Windows Encrypting File System for selected folders and sub-folders. This works perfectly for example to protect the temporary directory used by Xecrets Ez [Beta], ensuring that only someone logged on as yourself, or software running in your user context, can read the information. It is not possible to access it from another account, or from another computer by removing the hard drive etc.
EFS is essentially an integrated file encryption function, but either files are decrypted as they leave the encrypted location, or they are not (easily) useable from other locations. It is thus not a replacement for regular file encryption, but is a very good complement for temporary files on Windows.
To encrypt the Xecrets Ez [Beta] folder, use Windows Explorer and go to %LOCALAPPDATA%\Axantum, select the XecretsEz folder and check the "Encrypt content" checkbox, like this:
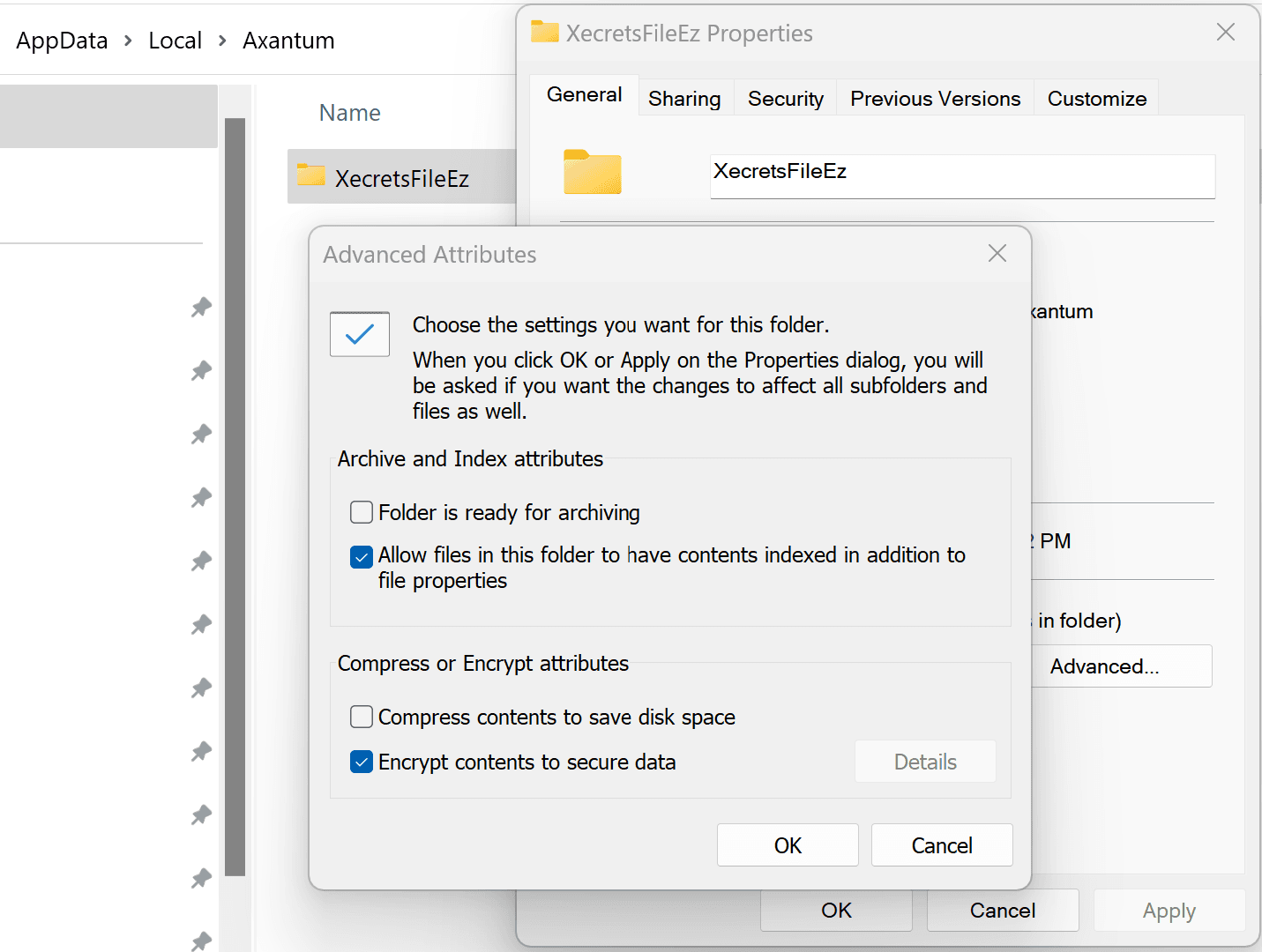
Warning: Contents of folders encrypted with EFS can be complicated to manage, and may be the single most common cause of data loss in Windows. In the normal case, the content is only decryptable on the original machine and by the original user account. A password reset (not a change) of such an account, will make the data impossible to decrypt, as will a re-installation of Windows. Do not use EFS for anything but temporary files, unless you fully understand how it works, and have stored a backup certificate in a secure separate location.
If for some reason you're not using full disk encryption, you may want to periodically erase the unused parts of your drive. When a file is deleted, it is typically not actually erased, the space occupied on the disk is just marked as free and available.
This means that deleted files can often be recovered, and there are many tools available that make this a pretty easy process. In fact, it can be useful at times when you realize you just deleted something that shouldn't have been deleted. If you need such a utility search and find one suitable for your needs.
There are some utilities that will help to truly erase, i.e. overwrite, all areas on the disk that are marked as free, thus ensuring left over data there can never be recovered or disclosed to unauthorized parties. We like eraser for Windows which has a long successful history, and you can of course search the web for other options.
To reduce the problem for particular files, use the Wipe feature of Xecrets Ez [Beta] instead of just deleting the file. Do remember that due to the way modern SSD drives work, the data may in fact still be possible to recover, but it requires a different level of utility than simple file system undelete.
If the other solutions do not fit your requirements, it is in some cases possible to use a RAM drive for temporary storage. This works by creating a virtual hard disk, that is in fact not really a hard disk, but instead uses your computers memory to simulate a hard disk.
This means that as soon as you power off your device, the memory is to all intents and purposes cleared and is entirely unrecoverable.
A nice side effect is that you'll have super-fast temporary storage, a less nice side effect is that it may need to consume significant parts of your devices' memory.
This used to be very popular before the advent of ubiquitous use of consumer level SSD drives, but the popularity has lessened with declining need. Nevertheless some solutions are available for various operating systems.